7 Sorts of Phishing Assaults You Should Know About
[ad_1]
The FBI estimates that Folks misplaced a whopping $12.5 billion to phishing schemes in 2023. You might assume you probably can set up a fraudulent e mail and avoid turning into a statistic; however, a malicious e mail is just considered one of many many phishing assaults cybercriminals use.
1 Piece of email Phishing
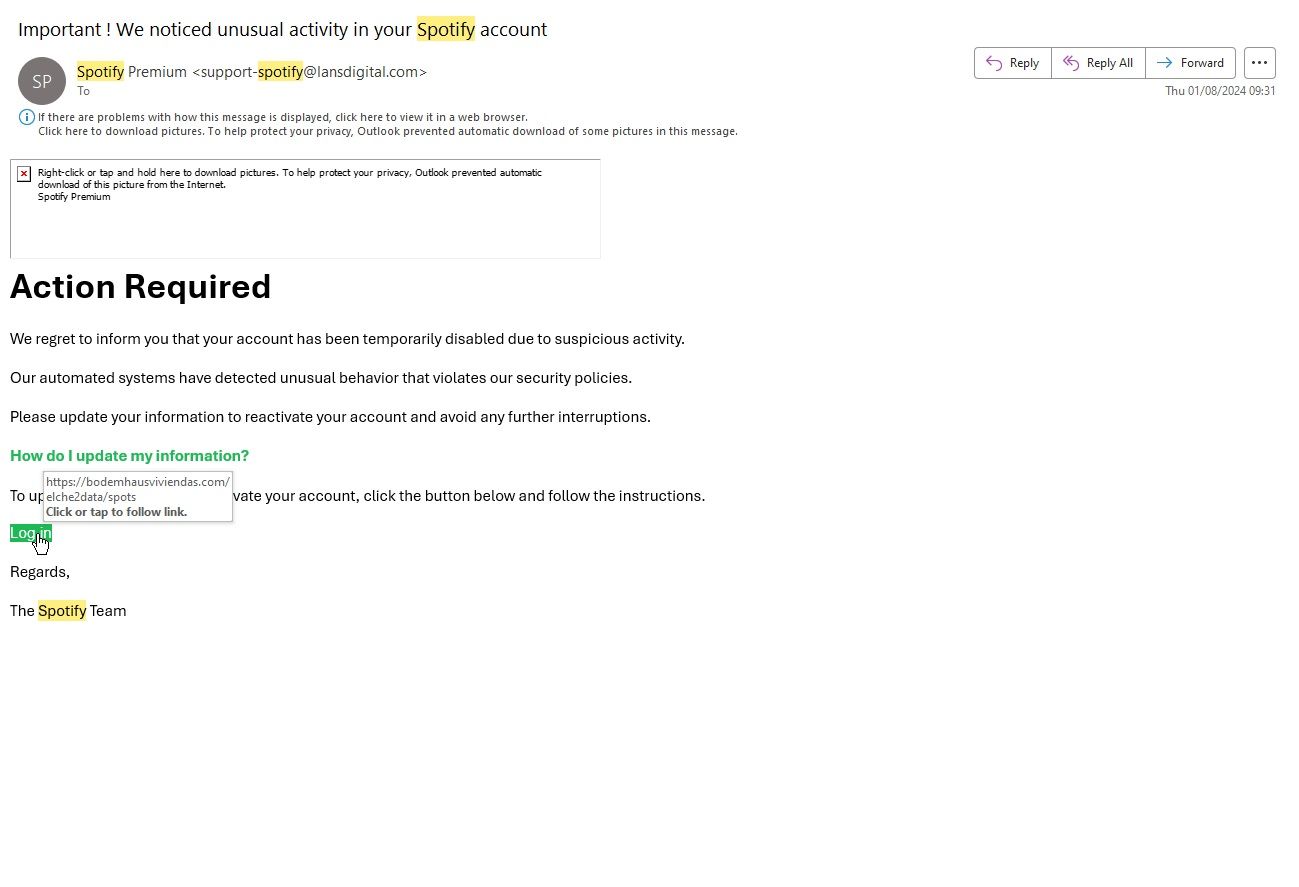
Initially, a phishing assault solely referred to an attempt to steal delicate data or money by the use of e mail. That’s because of e mail was considered one of many first assault vectors criminals used to rip-off of us on-line. It is nonetheless one of many very important trendy phishing schemes, with an estimated 3.4 billion emails despatched every single day, and is the FBI’s most reported crime.
The overwhelming majority of phishing emails was as soon as simple to ascertain. Poor grammar and odd phrase different had been lifeless giveaways that the e-mail was fake. That has modified given that rise of generative AI like ChatGPT, which helps hackers with no data of English quickly craft emails that will con anyone.
In case you are questioning if an e mail is precise, contact the alleged agency instantly, not by responding to the e-mail. And regardless of you do, if you’re unsure if an e mail is real, don’t click on on any hyperlinks or acquire any attachments.
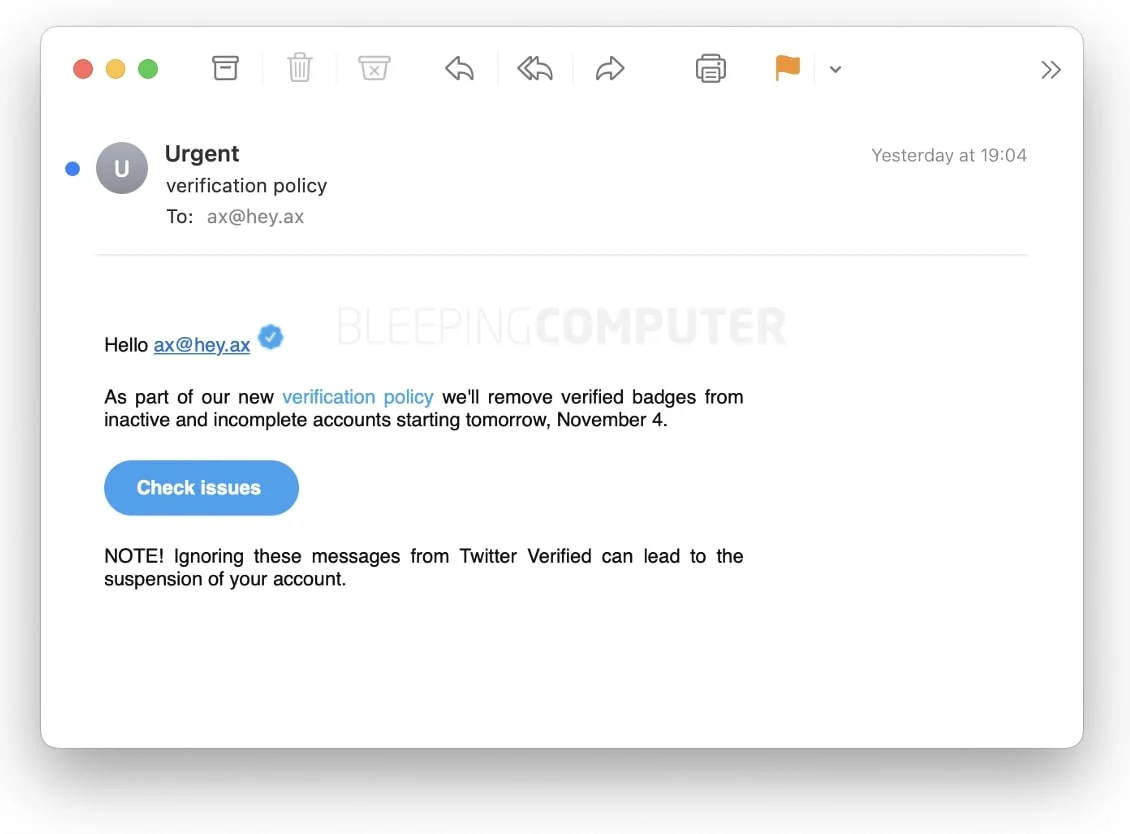
2 Smishing
Most people check a textual content material inside 5 minutes of receiving it because of texts, in distinction to emails, are usually despatched by associates, family, and companies we perception.
Smishing is an identical as e mail phishing, apart from instead of receiving a fraudulent e mail, you acquire an SMS. You’ve seemingly obtained a textual content material from Amazon alerting you of a bundle deal arrival no matter not placing an order. Or maybe you obtained a textual content material from a stranger who claims to have the fallacious amount nonetheless nonetheless insists on starting a dialog with you. Every are circumstances of a authorized attempting to have you ever ever click on on on malware or to dupe you into giving them money.
Pig butchering is an an increasing number of trendy smishing assault by which an attacker optimistic features your perception sooner than convincing you to spend cash on one factor (normally a pretend crypto change) and ultimately steals your funding.
3 Angler Phishing
We publish a wealth of information on social media for all to see. Scammers will use this data to create a extraordinarily custom-made angler phishing assault.
An attacker combs by way of your social media to review regarding the companies you utilize. They then pose as a buyer assist advisor from a company they’ve ascertained you utilize. They may ask for delicate particulars, ship a malicious hyperlink, or hyperlink to a pretend site to steal your password or totally different particulars they are going to use to entry your account.
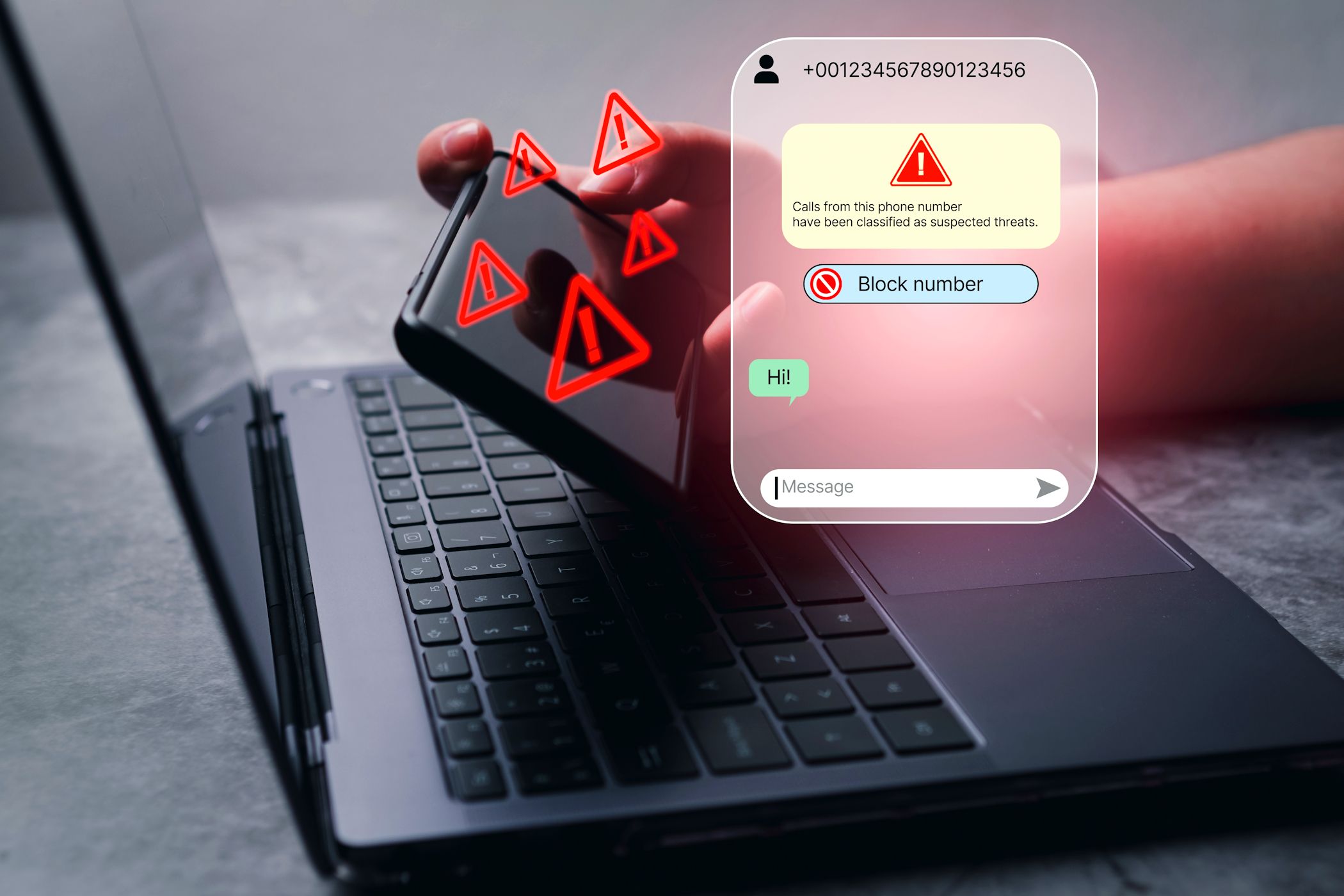
4 Vishing
Simply these days, a assured and cordial explicit particular person claiming to be from Wells Fargo phoned me to say a suspicious price had been made with my card and that they wished to substantiate my id. The very very first thing they requested for was my social security amount.
This vishing assault had every key ingredient a social engineering assault should succeed. They said that time was of the essence, scared me into almost giving them delicate data, and pretended to have the authority to ask for this data from me.
Fortuitously, scam-blocking choices and apps can reduce malicious calls, nonetheless it is best to nonetheless be cautious.
5 Spear Phishing
As talked about, billions of phishing emails are despatched every single day. Most of these are the an identical emails despatched out in bulk, pretending to come back again from a decent enterprise, nonetheless they don’t seem to be custom-made.
Spear phishing is a far more custom-made assault. Take into consideration if an e mail you obtained used your title and contained delicate data. Naturally, you’d be relatively extra inclined to open it.
Spear phishing assaults aren’t used on the standard explicit particular person; barely, they’re reserved for anyone the hacker deems to be of extreme value. A hacker might make investments time and money into gathering particulars about their objective to assemble a extraordinarily custom-made malicious e mail.
One variant of the spear phishing assault is “whaling,” which is used for even higher-value targets, akin to C-suite executives and CEOs.
6 Watering Hole
A watering hole assault works by compromising a decent site. Attackers can take over an entire site or uncover a vulnerability and inject HTML or JavaScript code that redirects clients to a spoofed site. As clients perception this site, they’re further extra prone to overtly click on on on hyperlinks and provide data akin to financial institution card data, social security numbers, and login credentials.
7 Web page Spoofing
Have you ever ever ever tried going to Amazon.com nonetheless accidentally typed Amazonn.com? No matter arriving at an web web site which can look and feel exactly like Amazon, it’s actually an impersonator site owned and operated by fraudsters. In a course of known as typosquatting, criminals purchase domains identical to trendy websites. They make these websites look comparable, apart from they’re wholly designed to collect your delicate data.
Whereas phishing assaults are getting harder to establish, you probably can maintain your self safe by refraining from clicking on hyperlinks or providing delicate data until you would have verified previous all doubt that the actual particular person you might be corresponding with is from the company in question.
[ad_2]
Provide hyperlink